
The Hidden Swarm: How Mini-Spy Processes Are Consuming Your Computer’s Resources
Introduction
Picture this: You’re working away at your computer — maybe on a big project, maybe just browsing — when you notice something’s off. The system feels sluggish. Perhaps it’s not dramatic enough to raise immediate alarms, but it’s there: a momentary lag, a stutter, an application that takes just a bit too long to open. You chalk it up to “normal” wear and tear. After all, everyone knows that PCs “just get slow over time,” right? The conventional wisdom is that machines naturally slow down over time, or that installing “too many programs” inevitably leads to bloat. But let’s challenge that assumption. What if this isn’t natural at all? What if, behind the scenes, your system is swarming with digital parasites — small processes constantly “calling home,” devouring your bandwidth and CPU cycles for their own research, telemetry, and profit?
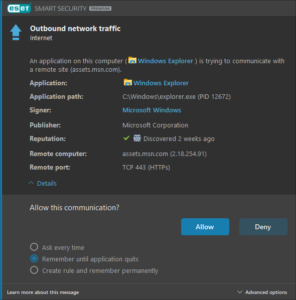
They’re not malware — at least not in the traditional sense. They’re your everyday applications and the OS itself they’re running on — your browser, your text editor, the word processor you trust, that “productivity tool” you installed six months ago — constantly “calling home,” checking for updates you don’t need yet, sending telemetry data you never approved, and extracting valuable insights from your system without your explicit, conscious consent. Under the guise of checking for updates or “improving user experience,” they make countless connections — sometimes every few seconds — using your computer and your network as test subjects, often with minimal user understanding or control.
Your computer and network become their testing ground, a resource pool they tap into for whatever reason — be it telemetry, analytics, updates, or something more nefarious. The saddest part is that many users are anesthetized to this reality. They’ve accepted it. They either don’t use a firewall at all, or they leave it on automatic mode, comforted by silence. When it comes to the barrage of background connections, ignorance feels like bliss. And so, the myth persists that PCs just get slower because that’s how it goes. In reality, this constant trickle of outbound connections — this digital feeding frenzy — contributes to that performance degradation. It’s not nature; it’s neglect.
But it doesn’t have to be this way.
The Endless Background Chatter: A Silent Epidemic of Secret Connections
In a perfect world, applications would only connect when necessary — once a day or week to check for updates, for example — instead of every five minutes. Yet the current norm is incessant pinging. Why? For some, it’s honest maintenance — verifying licenses, fetching legitimate updates. For others, it’s a constant data grab: usage patterns, system info, browsing tendencies. “Telemetry,” they call it, a benign-sounding word that cloaks a vast industry of user-data exploitation. Multiply this by dozens or hundreds of applications, and your system becomes a busy marketplace of data exchange you never explicitly sanctioned.
When dozens or hundreds of apps engage in these background pings, your machine’s resources are siphoned off bit by bit. Network traffic increases, CPU cycles are wasted, and your bandwidth allocation might resemble a party snack bowl — emptying out far too quickly as uninvited guests keep dipping in for more.
This leads to wasted resources — bandwidth, CPU, even battery life on laptops. Your machine becomes a resource buffet that software developers dine at around the clock.
Firewall Automatic Mode: A False Comfort
Many users assume their firewall is protecting them. They trust “automatic mode” or “smart mode” to handle the details. But these modes often grant free reign to “safe” applications. Yes, you’re spared the constant prompts, but you’re also left in the dark, never realizing how frequently these apps connect home. Meanwhile, the outbound chatter continues unchecked.
Switching to an interactive or “ask” mode can be illuminating but frustrating. Suddenly, every app’s hidden habits come into view. Prompts flood your screen: “Process X wants to connect,” “Y is checking for updates,” “Z wants to send data.” The onslaught can be overwhelming, driving many users right back to automatic mode. The status quo persists — software is designed to wear down your resolve, leaving you numb and compliant. Out of frustration, many just give up and revert to automatic mode, once again abandoning control.
This is the status quo the software industry thrives upon: user fatigue and resignation.
The Illusion of “Allow/Block and Remember for This Session”
One might think a good solution lies in the middle: choosing “allow/block and remember for this session” whenever prompted. In theory, this should let you temporarily allow or deny certain connections without committing permanently. But here’s the catch: software makers have learned to circumvent this. They employ launch agents and background daemons under different process names, or cycle through multiple helper processes that each require separate approvals. These techniques effectively reset the “session” and trick your firewall into asking again — or sometimes bypass your previous decision entirely.
As a result, “remember for this session” is not fool-proof. It feels like a neat compromise, but in reality, it can be exploited. After a few minutes or hours — if not seconds (!), you find yourself bombarded again. Some might argue that this half-measure is good enough, but the truth is that modern software is often too cunning, spawning new processes and daemons that repeatedly prompt you or slip through the cracks. Without a more robust system for managing outbound connections — one that accounts for such workarounds — your attempts to maintain control often fail.
This is the status quo the software industry thrives upon: user fatigue and resignation.
Taking Back Control: From Simple Solutions to Complex Needs
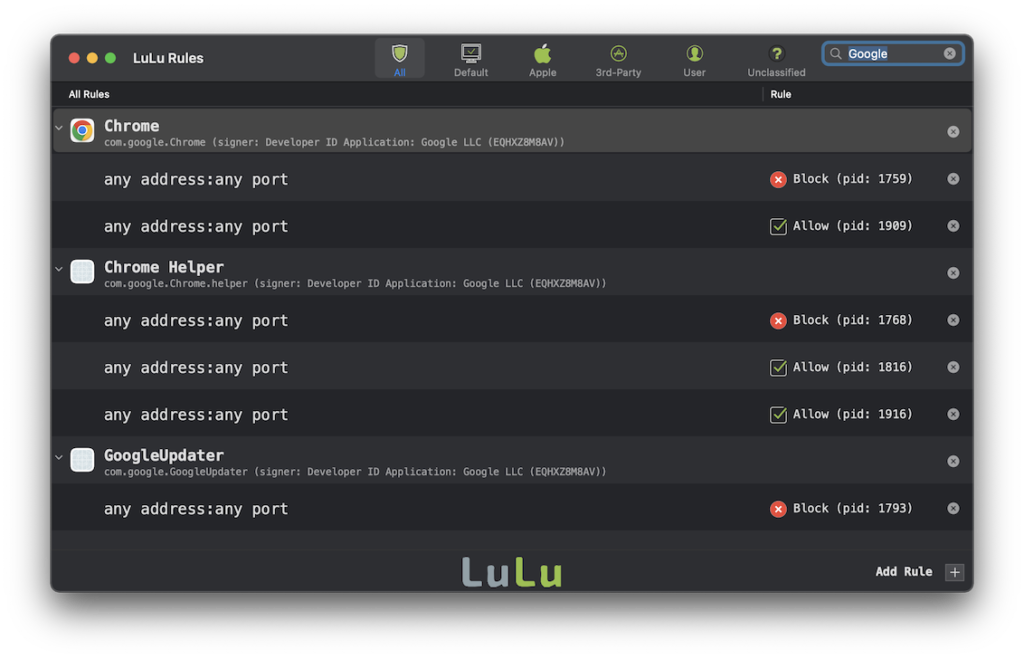
If you’re tired of this reality, you’re not alone. There are ways to fight back. On macOS, tools like Lulu, a free and open-source firewall by Objective-See, give you visibility into outbound connections. Another macOS favorite, Little Snitch, is a paid (about $45 one-time) but powerful tool offering granular control. You can block connections per-app, per-domain, and for limited time windows — i.e. per-time interval. Yet even these powerhouses don’t easily enable nuanced rules like “allow this process 30 times in the next 100 minutes, then block forever.”
On Windows, finding open-source indie equivalents that mirror Lulu’s philosophy isn’t straightforward. Portmaster by Safing (free, open-source) and Simplewall (also free, open-source) come close, empowering you with more insight and control than the Windows default. They help you reclaim some agency, but as with macOS tools, complex conditional logic remains rare. Meanwhile, commercial options like GlassWire (freemium) and NetLimiter (paid) improve user-friendliness but still lack the kind of deeply conditional, session-based blocking that could permanently thwart those pesky launch-agent tricks.
Dreaming of Conditional Rules
Imagine an ideal firewall where you can define rules like:
- “Allow at most 30 connections for this app over the next 100 minutes.”
- “After those 30 connections, block it permanently.”
- “If the app restarts under a different name, still treat it the same way.”
Such features remain mostly theoretical for consumer-level firewalls. To achieve them today, you’d likely need to script with macOS’s pf or tap into Windows Filtering Platform APIs. This is not for casual users and demands time, programming skills, and patience.
The Performance Angle: My Personal Experience with ESET and Intego on macOS
Some security suites claim cross-platform prowess. Yet, in my own experience, products like ESET Internet Security or Intego NetBarrier caused slowdowns and occasional instability on macOS. As someone who uses both macOS and Windows PCs simultaneously, I’m hopeful that major improvements will emerge in the near future. However, there appear to be no reliable third-party tests or reputable reviews highlighting any revolutionary changes in outbound firewall logic or performance impact. These tools still focus primarily on general security rather than offering advanced, session-based firewall rule management to thwart launch-agent trickery. In short, they’re built for the masses, not for power-users who demand perfect outbound clarity.
Educate, Advocate, and Collaborate
Users have been lulled into complacency. The barrage of background processes is normalized, and the idea that “PCs just slow down” is accepted as gospel. To break this cycle, we must educate ourselves and others. Discuss these issues on forums, social media, privacy subreddits, and local tech groups. Raise awareness that your machine’s sluggishness may not be “just how it is,” but a symptom of excessive, unnecessary outbound connections.
By demanding better tools — firewalls that can handle complex logic, track agent-based evasion, and truly empower the user — we can push developers to innovate. Indie developers behind Lulu or Portmaster might be more receptive to these suggestions, and open-source projects are open to community contributions. With enough interest, the now-exotic features we crave could become standard, putting control firmly back in users’ hands.
Call to Action: Potential Ready-Made Solutions
For macOS
Little Snitch:
- Little Snitch is the gold standard on macOS for outbound firewall control.
- Features include creating temporary rules, domain-based rules, and easily toggling rules on/off via a well-designed interface.
- You can set rules to expire after a certain time interval, a session, or until the next reboot. This might help with short-term blocking without committing to permanent rules.
Radio Silence:
- A simpler alternative to Little Snitch.
- Less interactive, but easier for quickly toggling on/off certain apps’ network access.
- Doesn’t prompt as often, but doesn’t have the granularity of time-based rules.
Lulu (Objective-See):
- You’re using Lulu. It’s effective but limited in terms of temporary rules and complex conditions.
- It’s open-source. You could reach out to the developer (Patrick Wardle) with feature requests. He’s known to be receptive to user feedback.
For Windows
GlassWire:
- A network monitoring tool with a firewall front-end.
- Offers a user-friendly interface to manage and visualize connections.
- You can easily toggle apps’ connections on and off without digging too deeply into complex interfaces. While it doesn’t provide “block for X hours” out-of-the-box, it’s easier to manage and quickly undo rules than ESET’s native interface.
Windows Firewall Control (from Malwarebytes):
- A front-end for the Windows native firewall.
- Offers a much more approachable interface than ESET or the built-in firewall alone.
- Lets you set rules and then easily find and toggle them later. While not as time-bound as you desire, it does simplify reversal of rules.
NetLimiter:
- Primarily a bandwidth control tool, but can also block connections.
- With filters and rules, you might simulate temporary blocking by toggling rules on and off as needed.
Proxifier / Fiddler:
- More developer-oriented tools that route all traffic through a proxy layer you control.
- If you’re comfortable with such tools, you can create dynamic rules, block domains for a session, and easily revert changes without messing with low-level firewall settings.
Advocating for Better Solutions
1. Contact Indie Developers (e.g., Objective-See for Lulu):
- They are often more responsive to feature requests.
- Suggest a “block until reboot” or “block for X minutes/hours” feature.
- Propose a “staging area” for rules where you can mass-enable/disable them later.
2. Lobby Larger Developers (ESET, BitDefender):
- File feature requests through their support channels.
- Explain the productivity hit caused by constant prompts.
- Emphasize that granular, temporary blocking features would set them apart from competitors.
3. Open-Source Contribution (if you are a developer or have enough coding skills):
- Contribute to open-source firewall projects.
- Add features like time-bound or circumstance-aware blocking rules.
Raising User Awareness
Blog / Social Media Advocacy:
- Write articles explaining why constant background connections are a problem.
- Show how to use tools like Little Snitch or Windows Firewall Control to mitigate them.
Community Forums & Tech Groups:
- Educate others about network privacy, the hidden cost of telemetry, and ways to reduce it.
- The more users demand these features, the more likely developers and security companies will listen.
Privacy-Focused Campaigns:
- Align with privacy and open-source communities (e.g., r/Privacy on Reddit, local privacy advocacy groups).
- Encouraging them to push developers for better firewall UX and features.
Conclusion: Your Computer, Your Rules
Your computer doesn’t have to be a resource buffet for every opportunistic app. With the right firewall tools, a bit of configuration, and some persistence, we should be able to restore balance. Recognize that “automatic mode” and half-measures like “block for this session” are easily exploited. Demand features that account for launch agents, rename-hacks, and incessant calling home. The goal is to starve the mini-spy parasites of their steady diet of data and CPU cycles.
Ultimately, your computer should serve you — not be a testing ground for software makers hungry for analytics and profits. By refusing to remain anesthetized and passive, you can take the first step toward a healthier, faster, more privacy-respecting digital life.
Tag:Client Security, Firewalls, Privacy

1 Comment
Excellent breakdown of how pervasive background telemetry and “mini-spy” processes silently drain performance. Most users underestimate how much system sluggishness comes from these constant outbound connections rather than hardware aging.
For anyone on Windows who wants to regain control, I’d recommend checking out Chris Titus Tech’s Windows Toolbox — it’s an open, script-based utility that can debloat Windows installations and disable many of Microsoft’s and third-party apps’ privacy-violating telemetry services. Used carefully, it’s one of the most effective ways to reduce background chatter without reinstalling the OS.
Also David Bombal’s video tutorial titled ‘Windows 11: Kill Telemetry, Widgets & Bloat’ is a must watch: https://www.youtube.com/watch?v=-E-WC_UvHXE